Beware: Some apps on Google Play infected with Windows malware
The infected APK files do not pose any threat to Android devices, as these embedded Windows .exe files can only run on Windows systems.
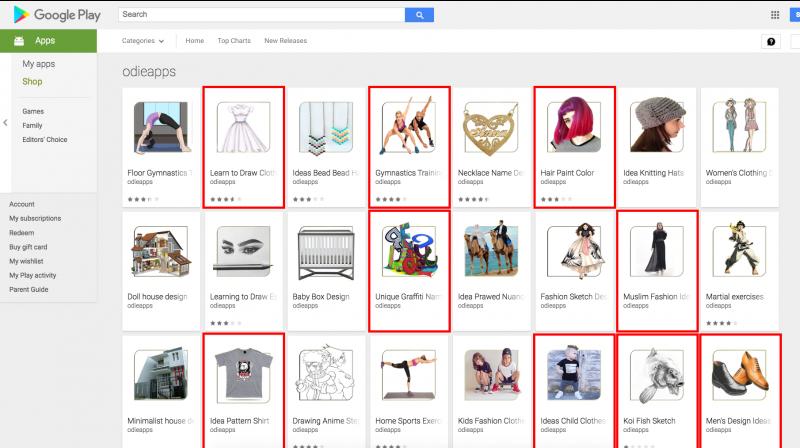
Last year, Unit 42 reported a number of Google play apps infected with malicious IFrames in this report. Recently, a similar case was found on Google Play. However, there are 145 Google Play apps found to be infected by malicious Microsoft Windows executable files instead of malicious IFrames. The findings have been reported to the Google Security Team and all infected apps have been removed from Google Play.
Notably, the infected APK files do not pose any threat to Android devices, as these embedded Windows executable binaries can only run on Windows systems — they are inert and ineffective on the Android platform. The fact that these APK files are infected indicates that the developers are creating the software on compromised Windows systems that are infected with malware. This type of infection is a threat to the software supply chain, as compromising software developers has proven to be an effective tactic for wide-scale attacks. Examples include KeRanger, XcodeGhost, and NotPetya.
Most of the infected apps were released to Google Play between October 2017 and November 2017, which means these apps have been in Google Play for more than half a year. Among these infected apps, several have more than 1,000 installations and 4-star ratings.
Interestingly, a mixture of infected and non-infected apps was discovered from the same developers. The reason might be that developers used different development environment for different apps.
Some of the infected apps include “Learn to Draw Clothing”, an app teaching people how to draw and design clothing; “Modification Trail”, an app showing images of trail bike modification ideas; “Gymnastics Training Tutorial”, an app letting people find healthy ideas for gymnastic moves.
Among these infected apps, one APK file may contain multiple malicious PE files at different locations, with different file names. However, there are mainly two PE files embedded across all of the infected apps.
According to the analysis results from WildFire, one PE file has infected 142 APK files including those apps on Google Play. The second PE file infected 21 APK files. 15 APK samples of them have both PE files mentioned above inside. Among these infected APK bundles, we found a number of other malicious PE files inside. These developers’ machines may be seriously infected by various malware families.
After investigating all those malicious PE files, it was found that there is one PE file which infects most of the Android apps, and the malicious activity of that PE file is keylogging. On a Windows system, this keylogger attempts to log keystrokes, which can include sensitive information like credit card numbers, social security numbers and passwords. Besides, these files fake their names to make their appearance look legitimate. Such names include “Android.exe”, “my music.exe”, “COPY_DOKKEP.exe”, “js.exe”, “gallery.exe”, “images.exe”, “msn.exe” and “css.exe”.
During Palo Alto Networks’ WildFire analysis, the malicious PE files have the following suspicious activities when executed on a Windows system:
- Creates executable and hidden files in Windows system folders, including copying itself
- Changes Windows registry to auto-start themselves after restarting
- Attempts to sleep for a long period
- Has suspicious network connection activities to IP address 87.98.185.184 via port 8829
Potential Damage and Mitigation
The malicious PE files cannot directly run on the Android hosts. However, if the APK file is unpacked on a Windows machine and the PE files are accidentally executed, or the developers also issue Windows-based software, or if the developers are infected with malicious files runnable on Android platforms, the situation will go much worse.
Customers of Palo Alto Networks are protected by WildFire and Traps for Android. WildFire is able to automatically detect these infected apps. Traps for Android protects Android devices, it automatically intercepts malicious apps installed on the device by leveraging WildFire and protect the device from malicious apps by blocking the app and notifying the user.
Click on Deccan Chronicle Technology and Science for the latest news and reviews. Follow us on Facebook, Twitter.

