Bad Rabbit creating havoc in Europe
The apparent ransomware worm, dubbed as BadRabbit', bubbled up and began spreading in Russia, Ukraine and other Eastern European countries.
Remember the last time ransomware exploded out of proportion? Two major international ransomware attacks that took place this year — NotPetya and Wannacry caused widespread disruption, affecting many at large. Now, reports of a new, and worse, ransomware have been discovered affecting computer systems across the European countries, once again showing that cybercriminals with malicious intentions to extort money from victims across the globe. For those who live under a rock, a ransomware is a type of program that locks infected computers and asks victims to pay ransom to restore access. The infamous ‘WannaCry’ ransomware attack in May forced the closure of factories, hospitals, and other facilities around the world for days.
The apparent ransomware worm, dubbed as ‘Bad Rabbit’, bubbled up and began spreading in Russia, Ukraine, and other Eastern European countries. The ransomware is said to be attacking corporate computers, several Russian media outlets, Ukraine’s Odessa airport and Kiev’s subway station as of now, according to a statement released by a Ukrainian government official.
Cybersecurity researchers — FireEye, ESET and Kaspersky, are among the organisations keeping strict watch online. Kaspersky found that both Petya and Bad Rabbit appeared on dozens of the same hacked websites, as stated by a report from Wired. According to ESET, the method used to distribute Bad Rabbit was through drive-by download, where Javascript is injected into website’s HTML body or a JS file. Any user who visits a compromised site is greeted by a pop-up, showing Flash Player needs to be updated, which in turn tricks victims into downloading and installing the malware themselves. ESET believes this was only one method and possibly a ‘smokescreen’.
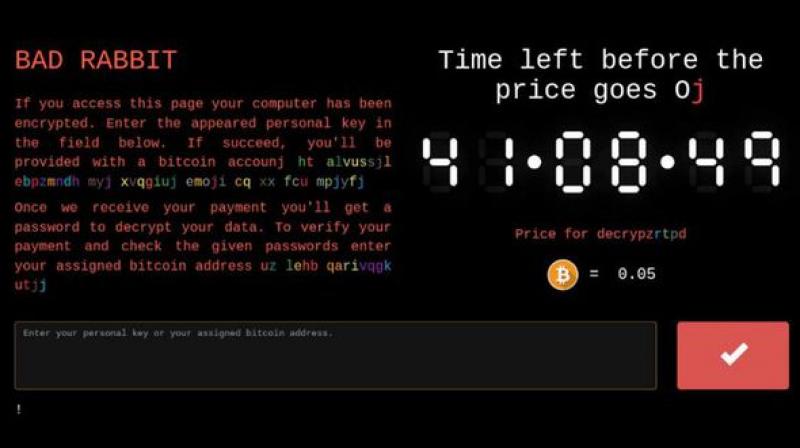
Once a computer is infected, the crooks behind Bad Rabbit lockdown computers and demand 0.05 Bitcoin (about $275) from victims within 41 hours in exchange for decryption of the data and restoring access to their machine. If the time expires, the ransom amount is bumped up. Although researchers believe that Bad Rabbit is somewhat similar to the Petya ransomware, it is still unclear as to who is behind the recent attack.
“Our network devices blocked infection attempts at multiple victims globally until around 2017-10-24 15:00:00 UTC when the infection attempts ceased and attacker infrastructure — both 1dnscontrol.com and monitored sites containing the rogue code — were taken offline. The use of strategic web compromises and profilers provide guardrails that allow attackers to select targets carefully and halt operations quickly,” said FireEye.
“When we say strategic web compromises, this means an attacker hosts malicious code on an unknowing victim’s website that is then used to infect the true targets. The websites are carefully selected for compromise so that they will have the most direct reach to the ultimate targets with minimal collateral damage. In the case of BadRabbit, many strategic compromises were Eastern European travel and media websites used to then profile visitors and deliver the payload,” they added.
We advise our readers to look for suspicious prompts or pop-ups on various websites. It is also advisable to use proper data security solutions such as antivirus software and anti-malware tools.

