Experts on cyber attack: Protect your PCs with software updates, don't pay ransoms
The programme was designed in such a manner that when it lands on a system it locks up all files and encrypts.
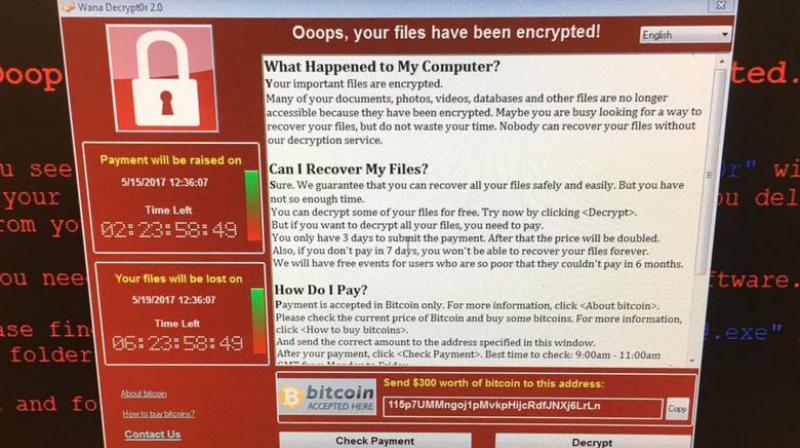
Friday’s ransomware cyber attack hard hit about 150 countries, infecting more than 200,000 machines worldwide and asking for ransom amount of $300 in Bitcoin to restore the affected systems to normal.
The hackers were found to inject the virus using a worm application called “WannaCry” that replicates itself in order to spread to other computers.
The programme was designed in such a manner that when it lands on a system it locks up all files and encrypts them in a way that one cannot access them anymore, until a ransom amount of $300 Bitcoin is paid—which defines the word ransomware.
There are many types of cyber attacks, but the one which prevents users form accessing their device until a certain amount of money is paid in digital currency are called ransomware.
And that’s what the hackers behind the recent ransomware attack demand—Money.
But the question is, will machines return to normal functioning when the demanded payment is made?
A Twitter bot tracking Bitcoin payments to digital wallet linked to the attack reveals the some people are willing to make payments in hope to restore their data and systems.
The three bitcoin wallets tied to #WannaCry ransomware have received 233 payments totaling 38.06273688 BTC ($64,472.33 USD).
— actual ransom (@actual_ransom) May 16, 2017
But many security experts are warning victims to not to pay the ransom.
In a webcast on Monday, India’s Computer Emergency Response Team (CERT-In) advised victims to not pay the ransom amount. “Do not pay the ransom,that will encourage the attackers to do more of such attacks. Report the incident to CERT-In and the local law enforcement agencies so that we can work on it,” CERT-In said in the webcast.
The European law enforcement agency Europol also warned paying up doesn't guarantee that you'll get everything back. And giving the hackers what they want proves the worm is effective.
"As a result, cybercriminals will continue their activity and look for new ways to exploit systems that result in more infections and more money in their accounts," Europol said in a statement.
Instead, the victims are being advised to apply patches to their Microsoft operating system Windows to prevent getting infected by the attack.
Those unaware, the ransomware used a bug in a Windows Server component spread the virus. The vulnerability was first discovered by America’s National Security Agency (NSA). It was later stolen by a group of hackers calling themselves “Shadow Brokers”.
Security experts have claimed the attackers of recent attack took advantage of the same vulnerability found in Windows OS to implant the virus.
Fortunately, the does not exist within Windows 10; however it is present in all version of former Windows OS, dating back to the Windows XP. This is the reason why many security experts are advising victims to upgrade their Windows OS to the latest version to protect their computers against the cyber attack.

