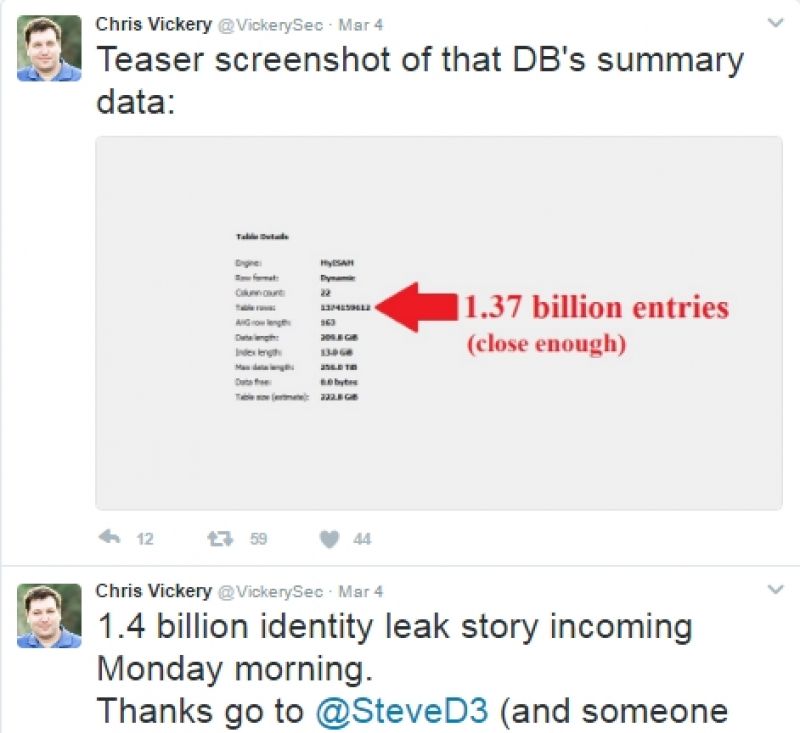
Spammers expose 1.4 billion emails via faulty backups

A database of about 1.4 billion email addresses has been leaked by one of the largest spamming operations in the world due to a failing backup configuration of its entire operation.
The spam operation has gathered and conglomerated a database of 1.4 billion individual email addresses, full names, IP addresses, and other physical addresses, according to security researchers at MacKeeper.
“The situation presents a tangible threat to online privacy and security as it involves a database of 1.4 billion email accounts combined with real names, user IP addresses, and often physical address,” said Chris Vickery, a security researcher at Mackeeper.
“Chances are that you, or at least someone you know, are affected,” he added.
The leaked information represents the backbone operation of a marketing firm called River City Media (RCM), responsible for up to a billion daily emails it sends across the world.
Vickery is still investigating on the credibility of the leaked data, but claims he has found addresses, which he says is accurate in the database. “It is a type of Slowloris attack,” Vickery said, “purposely throttling your own machinery to amass open connections on someone else’s server.”
He explained it is a “technique in which the spammer seeks to open as many connections as possible between themselves and a Gmail server. This is done by purposefully configuring your own machine to send response packets extremely slowly, and in a fragmented manner, while constantly requesting more connections. Then, when the Gmail server is almost ready to give up and drop all connections, the spammer suddenly sends as many emails as possible through the pile of connection tunnels. The receiving side is then overwhelmed with data and will quickly block the sender, but not before processing a large load of emails.”
“Well-informed individuals did not choose to sign up for bulk advertisements over a billion times,” Vickery said. “The most likely scenario is a combination of techniques. One is called co-registration. That’s when you click on the “Submit” or “I agree” box next to all the small text on a website. Without knowing it, you have potentially agreed your personal details can be shared with affiliates of the site.”
As the size of the breach is large, the India’s Aadhaar UID system, which individually holds a database of more than a billion citizens, could have been considered among possible sources for the breach.
However, in a publically released statement, issued on Sunday, the Ministry of Electronics and IT (MEITY), India, denied allegations over the misuse of Aadhaar biometrics. “There has been no incident of misuse of Aadhaar biometrics leading to identity theft and financial loss during the last five years when more than 400 crore Aadhaar authentication transactions have taken place, according to Unique Identification Authority of India (UIDAI),” MEITY stated.